Microsoft new initiative "Local Administrator Password Management" or also known as "LAPS" clearly shows how serious they are about the "Security" domain that they have launched a new tool to enhance the security on the client machines (They could have incorporated this in the next version of their Operating System but it seems that they didn't wanted to waste any time waiting for the release of the newer version)
With LAPS, there are few points to be noted:-
- Administrator Account (And keep this in mind, I did not said "The Administrator Account" which the the default administrator account) will get a "RANDOM" Password
- The Password on all the machines will be DIFFERENT
- These Passwords will be STORED in Active Directory under the Machine Account
Lets see how this so called LAPS works !!!!
For the lab purpose, I have a domain "ADShotGyan", Domain Controller (DC1 - Windows 2012 R2) and Client Machine (Win7 - Windows 7)
You can download LAPS from the following location:
https://www.microsoft.com/en-us/download/details.aspx?id=46899
Currently, I am on a Windows 2012 R2 Domain Controller
The "Welcome" Page
"I Agree"... As if you had any other option...
There are two main components of LAPS:
- AdmPwd GPO Extension
- Management Tools
- Fat Client UI
- PowerShell Module
- GPO Editor Template
The GPO Extensions are the CSE`s (Client Side Extensions) for LAPS and need to be installed on all the client machines which you as an administrators wants to manage
Rest of the management tools are optional on client machines but you will need them on the domain controller from where you want to manage LAPS
Click on Install....
At this point, If I look at the properties of any computer object, I wont be able to see any new attributes populated.
We need to install the same tool on the client machines as well on which we want to configure the local administrators password
An important thing to note is that we DON'T have to install all the components. We just need to install the "GPO Extensions"
Install...
Once the installation is completed, browse through the "Programs and Features" on the client machine and you will find the "Local Administrator Password Solution"
This will install the required dll (AdmPwd.dll) on the following location:
C:\Program Files\LAPS\CSE
Do Register this dll (AdmPwd.dll)
Lets come back on to the server
We first need to import the following module using PowerShell
Import-Module AdmPwd.PS
Then, Update the Schema....
Update-AdmPwdADSchema
The Schema Update will Add the following Attributes:
- ms-Mcs-AdmPwdExpireationTime
- ms-Mcs-AdmPwd
And you should be then able to view these attributes on any machine account
Permissions
Now lets see which all permissions do we have on these machines w.r.t LAPS
Understand this... With LAPS, Administrator Account on every machine will have a random password and this password will be stored in the machine account in active directory. So the machine need to have rights on the attributes where the password will be stored
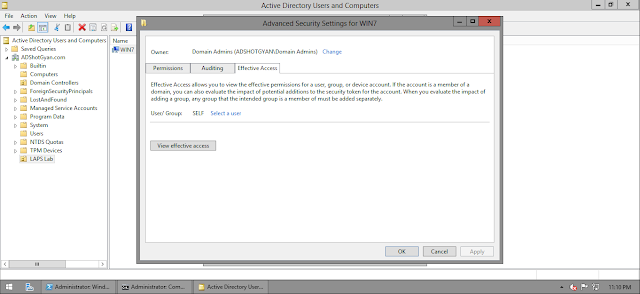
Lets have a look on these permissions on a machine account
We need to look for the permission for the SELF account on the machine account
hmm... That`s strange.. So the SELF account do not have any rights on the attributes which will store the password... Which simply means that this wont work..
Read ms-Mcs-AdmPwd
Write ms-Mcs-AdmPwd
Read ms-Mcs-AdmPwdExpirationTime
Write ms-Mcs-AdmPwdExpirationTime
So now lets give those permissions
Set-AdmPwdComputerSelfPermission -OrgUnit <OU where the Client Machines are Stored>
Example:
Set-AdmPwdComputerSelfPermission -OrgUnit "OU=LAPS Lab,DC=ADShotGyan,DC=com"
Delegated...
Now lets have a look on the permissions again
Now SELF has rights on the attributes
Write ms-Mcs-AdmPwd
Read ms-Mcs-AdmPwdExpirationTime
Write ms-Mcs-AdmPwdExpirationTime
Note that it still does not have rights on the attribute "Read ms-Mcs-AdmPwd"
The above permission which we gave was for the machine account. But what if an administrator wants to READ the administrator password stored on the machine account. Even though the password which will be generated will be a random password but then the domain administrator should be able to read the password else how would they be able to use that password on the machine for which the password has been generated
Currently, we have two administrator accounts in ADSHOTGYAN.COM domain
- Sumit Sethi
- Administrator
And they both don't have any rights/permissions on this computer account
So lets give them the permissions
Set-AdmPwdReadPasswordPermission -OrgUnit "OU=LAPS Lab,DC=ADShotGyan,DC=com" -AllowedPricipals "ADShotGyan\Sumit Sethi","ADShotGyan\Administrator"
Delegated...
Now "Sumit Sethi" has been added in this computer account ACLs
And "Sumit Sethi" has Full Control
Similarly, We have created another account named "Reset" who will have the delegated permission on the computer account to reset the password of the administrator account
Notice the difference in the two commands...
We gave "Sumit Sethi" and "Administrator" accounts "READ" Permissions and "Reset" account "RESET" Permission
Set-AdmPwdResetPasswordPermission -OrgUnit "OU=LAPS Lab,DC=ADShotGyan,DC=com" -AllowedPricipals "ADShotGyan\Reset"
Delegated ....
Read & Reset....
Lets verify the permissions "Reset" account has now got on this computer account
Note that the "Reset" account has not got Full Control...
Now lets explore the Group Policies associated with LAPS
Location:
Computer Configuration -> Administrative Templates -> LAPS
Settings:
- Password Settings
- Name of administrator account to manage
- Do not allow password expiration time longer than required by policy
- Enable local admin password management
Password Settings
It defines the password complexity settings
Name of administrator account to manage
If you are a good admin, then you will always rename your default built in admin account or you keep your built in administrator account disabled and will create a secondary administrator account with some other name as the default admin account "administrator" can be easily hack-able
So, if you have a second administrator account on client machines then you can specify that account name here in the group policy setting
Do not allow password expiration time longer than required by policy
Enable local admin password management
When enabled, local administrator password is managed
Now we have rebooted a client machine and a password got generated which is stored in the attribute on the client machine account
On the client machine, lets enable the default administrator account
Note: We reset the default administrator account on the client machine but the password on the client machine account in active directory remained unchanged. So the password which is stored in active directory is only the password which has been generated by LAPS and not the one which you as an administrator will reset on the account on the client machine manually
On the domain controller, lets open the LAPS Management UI
Enter the Client Machine Name
And it will display the Password and the Expiration Time
Click on Set and it will Reset the Password. Note that the expiration date has now changed
To confirm, the new password has now been populated in active directory in that machine account
Lets do some testing with the custom "Admin" account present on the client machine
Lets configure the policy "Name of administrator account to manage" and add "Admin" account name in that setting
Note that the password is still the old one which was associated with the default "Administrator" account
Even if we disable the administrator account, the same password cannot be used
We have to generate a new password which would then be assigned to the new custom administrator account "Admin"
Also an important point to note here is that if we have the built in administrator account and a custom account with no setting for the custom account defined then the generated password will be assigned to the default administrator account. Howe ever, if we have a custom admin account and the same account is mentioned in the group policy setting as well, then that account will get the generated password even if the default administrator account is enabled on the client machine
Earlier we had created a "Reset" account which had the permission to reset the password
Now we have created another account "NoReset" which doesn't have the reset permission
Lets logon to the client machine as the "NoReset" account and try to reset the password
"Failed to Request Password Reset"
Lets logon to the client machine as the "Reset" account and try to reset the password
"Password Reset Request was Successful"
But did you notice something in the above window. Even though the Reset account was able to reset the password, however the account was unable to read the password. the password attribute in the Management UI was empty. This is because the Reset account only had the Reset permission and not the Read permission
Now lets give Read permission to the Reset Account
Set-AdmPwdReadPasswordPermission -OrgUnit "OU=LAPS Lab,DC=ADShotGyan,DC=com" -AllowedPricipals "ADShotGyan\Reset"
Now the Reset Account is able to Reset and Read Password
With LAPS, there are few points to be noted:-
- Administrator Account (And keep this in mind, I did not said "The Administrator Account" which the the default administrator account) will get a "RANDOM" Password
- The Password on all the machines will be DIFFERENT
- These Passwords will be STORED in Active Directory under the Machine Account
Lets see how this so called LAPS works !!!!
For the lab purpose, I have a domain "ADShotGyan", Domain Controller (DC1 - Windows 2012 R2) and Client Machine (Win7 - Windows 7)
You can download LAPS from the following location:
https://www.microsoft.com/en-us/download/details.aspx?id=46899
Currently, I am on a Windows 2012 R2 Domain Controller
The "Welcome" Page
"I Agree"... As if you had any other option...
There are two main components of LAPS:
- AdmPwd GPO Extension
- Management Tools
- Fat Client UI
- PowerShell Module
- GPO Editor Template
The GPO Extensions are the CSE`s (Client Side Extensions) for LAPS and need to be installed on all the client machines which you as an administrators wants to manage
Rest of the management tools are optional on client machines but you will need them on the domain controller from where you want to manage LAPS
Click on Install....
At this point, If I look at the properties of any computer object, I wont be able to see any new attributes populated.
We need to install the same tool on the client machines as well on which we want to configure the local administrators password
An important thing to note is that we DON'T have to install all the components. We just need to install the "GPO Extensions"
Install...
Once the installation is completed, browse through the "Programs and Features" on the client machine and you will find the "Local Administrator Password Solution"
This will install the required dll (AdmPwd.dll) on the following location:
C:\Program Files\LAPS\CSE
Do Register this dll (AdmPwd.dll)
Lets come back on to the server
We first need to import the following module using PowerShell
Import-Module AdmPwd.PS
Then, Update the Schema....
Update-AdmPwdADSchema
The Schema Update will Add the following Attributes:
- ms-Mcs-AdmPwdExpireationTime
- ms-Mcs-AdmPwd
And you should be then able to view these attributes on any machine account
Permissions
Now lets see which all permissions do we have on these machines w.r.t LAPS
Understand this... With LAPS, Administrator Account on every machine will have a random password and this password will be stored in the machine account in active directory. So the machine need to have rights on the attributes where the password will be stored
Lets have a look on these permissions on a machine account
We need to look for the permission for the SELF account on the machine account
hmm... That`s strange.. So the SELF account do not have any rights on the attributes which will store the password... Which simply means that this wont work..
Read ms-Mcs-AdmPwd
Write ms-Mcs-AdmPwd
Read ms-Mcs-AdmPwdExpirationTime
Write ms-Mcs-AdmPwdExpirationTime
So now lets give those permissions
Set-AdmPwdComputerSelfPermission -OrgUnit <OU where the Client Machines are Stored>
Example:
Set-AdmPwdComputerSelfPermission -OrgUnit "OU=LAPS Lab,DC=ADShotGyan,DC=com"
Delegated...
Now lets have a look on the permissions again
Now SELF has rights on the attributes
Write ms-Mcs-AdmPwd
Read ms-Mcs-AdmPwdExpirationTime
Write ms-Mcs-AdmPwdExpirationTime
Note that it still does not have rights on the attribute "Read ms-Mcs-AdmPwd"
The above permission which we gave was for the machine account. But what if an administrator wants to READ the administrator password stored on the machine account. Even though the password which will be generated will be a random password but then the domain administrator should be able to read the password else how would they be able to use that password on the machine for which the password has been generated
Currently, we have two administrator accounts in ADSHOTGYAN.COM domain
- Sumit Sethi
- Administrator
And they both don't have any rights/permissions on this computer account
So lets give them the permissions
Set-AdmPwdReadPasswordPermission -OrgUnit "OU=LAPS Lab,DC=ADShotGyan,DC=com" -AllowedPricipals "ADShotGyan\Sumit Sethi","ADShotGyan\Administrator"
Delegated...
Now "Sumit Sethi" has been added in this computer account ACLs
And "Sumit Sethi" has Full Control
Similarly, We have created another account named "Reset" who will have the delegated permission on the computer account to reset the password of the administrator account
Notice the difference in the two commands...
We gave "Sumit Sethi" and "Administrator" accounts "READ" Permissions and "Reset" account "RESET" Permission
Set-AdmPwdResetPasswordPermission -OrgUnit "OU=LAPS Lab,DC=ADShotGyan,DC=com" -AllowedPricipals "ADShotGyan\Reset"
Delegated ....
Read & Reset....
Lets verify the permissions "Reset" account has now got on this computer account
Note that the "Reset" account has not got Full Control...
Now lets explore the Group Policies associated with LAPS
Location:
Computer Configuration -> Administrative Templates -> LAPS
Settings:
- Password Settings
- Name of administrator account to manage
- Do not allow password expiration time longer than required by policy
- Enable local admin password management
Password Settings
It defines the password complexity settings
Name of administrator account to manage
If you are a good admin, then you will always rename your default built in admin account or you keep your built in administrator account disabled and will create a secondary administrator account with some other name as the default admin account "administrator" can be easily hack-able
So, if you have a second administrator account on client machines then you can specify that account name here in the group policy setting
Do not allow password expiration time longer than required by policy
Enable local admin password management
When enabled, local administrator password is managed
Now we have rebooted a client machine and a password got generated which is stored in the attribute on the client machine account
On the client machine, lets enable the default administrator account
Note: We reset the default administrator account on the client machine but the password on the client machine account in active directory remained unchanged. So the password which is stored in active directory is only the password which has been generated by LAPS and not the one which you as an administrator will reset on the account on the client machine manually
On the domain controller, lets open the LAPS Management UI
Enter the Client Machine Name
And it will display the Password and the Expiration Time
Click on Set and it will Reset the Password. Note that the expiration date has now changed
To confirm, the new password has now been populated in active directory in that machine account
Lets do some testing with the custom "Admin" account present on the client machine
Lets configure the policy "Name of administrator account to manage" and add "Admin" account name in that setting
Note that the password is still the old one which was associated with the default "Administrator" account
Even if we disable the administrator account, the same password cannot be used
We have to generate a new password which would then be assigned to the new custom administrator account "Admin"
Also an important point to note here is that if we have the built in administrator account and a custom account with no setting for the custom account defined then the generated password will be assigned to the default administrator account. Howe ever, if we have a custom admin account and the same account is mentioned in the group policy setting as well, then that account will get the generated password even if the default administrator account is enabled on the client machine
Earlier we had created a "Reset" account which had the permission to reset the password
Now we have created another account "NoReset" which doesn't have the reset permission
Lets logon to the client machine as the "NoReset" account and try to reset the password
"Failed to Request Password Reset"
Lets logon to the client machine as the "Reset" account and try to reset the password
"Password Reset Request was Successful"
But did you notice something in the above window. Even though the Reset account was able to reset the password, however the account was unable to read the password. the password attribute in the Management UI was empty. This is because the Reset account only had the Reset permission and not the Read permission
Now lets give Read permission to the Reset Account
Set-AdmPwdReadPasswordPermission -OrgUnit "OU=LAPS Lab,DC=ADShotGyan,DC=com" -AllowedPricipals "ADShotGyan\Reset"
Now the Reset Account is able to Reset and Read Password